
Just days ago, on December 29, 2025, the world witnessed one of Germany’s most audacious bank heists in recent history. During the quiet of the Christmas holiday, a group of highly organized criminals executed what police described as a “very professionally executed” operation—they drilled a massive hole through thick concrete walls from an adjacent parking garage, breaching the Sparkasse Bank vault in Gelsenkirchen and accessing over 3,000 safe deposit boxes. The estimated losses range from $11.7 million to a staggering $105.7 million.
This wasn’t a spur-of-the-moment crime. It required extensive planning, insider knowledge of the bank’s layout, specialized drilling equipment, and precise execution timing. The thieves worked methodically over the Christmas weekend when the bank was closed, emerging only when their job was complete. By the time a fire alarm triggered at 3:58 AM on December 29, they had vanished—leaving behind only a gaping hole and thousands of ransacked deposit boxes.
For Indian banks, this incident isn’t just international news—it’s a wake-up call. Similar underground vault attacks have already occurred on Indian soil, and the threat is escalating as criminal syndicates grow more sophisticated, better financed, and increasingly willing to invest months in planning a single high-value heist.
Key Insight: Underground vault attacks represent a paradigm shift in banking security threats. Traditional above-ground security measures provide zero protection against criminals who create their own entry points through basement floors, adjacent properties, or underground tunnels.
Indian financial institutions are no strangers to underground vault attacks. In recent years, several high-profile incidents have exposed the vulnerability of traditional vault security systems:
In December 2022, thieves executed a meticulously planned attack on the State Bank of India’s Bhanuti branch in Kanpur, Uttar Pradesh. The criminals dug a 10-feet-long and four-feet-wide tunnel from an empty plot adjacent to the bank, directly into the vault’s strong room. They successfully stole over 1.8 kg of gold worth approximately ₹1 crore. Despite the bank having traditional security measures including CCTV cameras and security personnel, the underground approach bypassed all visible defenses entirely.
Police investigations revealed that the robbery was likely an inside job, with expert criminals working in coordination with someone who had intimate knowledge of the bank’s layout, vault construction, and security protocols. The tunnel itself demonstrated sophisticated engineering—the thieves had studied the architecture carefully to determine the precise location to break through.
In November 2017, a gang of robbers executed an even more elaborate scheme at the Bank of Baroda’s Juinagar branch in Navi Mumbai. Over approximately five months, the criminals rented a nearby general store called “Shri Balaji” and systematically constructed a 25-30 feet tunnel leading directly to the bank’s locker room. They reinforced the tunnel ceiling with ply sheets and bamboo props to prevent collapse—a level of planning that indicated professional experience.
The robbery occurred over a weekend, and CCTV footage later showed three men casually walking out of the shop, carrying bags containing valuables worth ₹3 crore from 30 breached lockers. The crime only came to light when the bank reopened on Monday morning. Like the Kanpur case, this attack completely circumvented the bank’s above-ground security infrastructure.
Pattern Analysis: Both Indian cases share common characteristics with the Germany heist:

Definition: Traditional bank security systems are designed on the assumption that threats will arrive through conventional entry points—doors, windows, and above-ground walls. This design philosophy creates a critical blind spot: the underground dimension.
The fundamental problem with most bank vault security systems in India today is that they’re designed to detect threats that arrive through conventional entry points—doors, windows, roofs, and walls at ground level. Traditional security measures include:
When criminals approach from below—drilling through basement floors, vault foundations, or adjacent underground spaces like parking garages, sewers, or neighboring properties—these conventional systems provide zero detection capability. By the time the breach is discovered, criminals have had hours or even days of uninterrupted access to deposit boxes and vault contents.
| Security Layer | Traditional System | Underground Attack Reality |
|---|---|---|
| Perimeter Protection | Fence sensors, gates | ✗ Bypassed via adjacent property |
| Building Shell | Window/door contacts | ✗ No detection of floor/foundation breach |
| CCTV Coverage | Monitors entrances, lobby | ✗ Cannot see underground activity |
| Vault Door | Time locks, biometrics | ✗ Rendered irrelevant when walls breached |
| Motion Sensors | Detect movement inside vault | ✗ Only triggers after breach complete |
| Response Time | After breach discovered (12–48 hours) | ✗ Criminals long gone |
The result: By design, traditional systems have a 12-48 hour detection delay for underground attacks—more than enough time for organized criminals to complete their operation and disappear.
According to a 2024 joint assessment by FATF-APG-EAG, India faces serious organized crime threats including money laundering and financial fraud. While India has implemented strong anti-money laundering frameworks, the physical security infrastructure at many bank branches—particularly those in tier-2 and tier-3 cities—has not kept pace with evolving criminal methodologies.
India’s financial sector is facing unprecedented security challenges on multiple fronts. According to recent government data reported in Economic Times and Business Standard:
While much attention has focused on digital threats, physical vault security breaches represent another significant vulnerability. Each successful vault heist not only results in immediate financial losses but also:
The Reserve Bank of India has significantly strengthened its cybersecurity and operational resilience framework in 2024-2025, mandating:
While these guidelines primarily address cyber threats, the underlying principle applies equally to physical security: banks must implement proactive, intelligent, continuously monitored security systems that can detect threats in real-time, not just respond after a breach has occurred.
Definition: AIoT (Artificial Intelligence of Things) combines IoT sensors with AI and machine learning algorithms to create security systems that analyze patterns in real-time, distinguish genuine threats from false alarms, and provide contextual intelligence to security teams.
AIoT combines traditional IoT sensors with artificial intelligence and machine learning algorithms to create security systems that don’t just collect data—they understand it. Unlike conventional alarm systems that simply trigger when a threshold is breached, AIoT systems:
| Feature | Traditional Security | AIoT Security (Atigo) |
|---|---|---|
| Detection Method | Threshold breach only | Pattern analysis + AI learning |
| Underground Threat Detection | ✗ None | ✓ Vibration / seismic sensors |
| False Alarm Rate | 90–98% (industry average) | 15–25% (60–85% reduction) |
| Response Time | Hours to days | Minutes (real-time alerts) |
| Attack Stage Detection | After breach complete | During preparation / drilling |
| Multi-sensor Integration | Limited or none | Full sensor fusion |
| 24/7 Monitoring | Optional add-on | Integrated service |
| Learning Capability | ✗ Static rules | ✓ Adaptive AI algorithms |
| Connectivity | Single channel | Multi-channel (Wi-Fi, GSM, Bluetooth) |
| Encryption | Basic or none | Military-grade AES-256 |
| Indian Climate Reliability | Often fails in extreme conditions | Engineered for 40°C+, 90% humidity |
Definition: Seismic sensors detect minute vibrations in walls, floors, and foundations by measuring mechanical oscillations. Advanced models use piezoelectric technology combined with AI algorithms to distinguish between normal ambient vibrations and attack signatures.
These are the frontline defense against drilling and tunneling attacks. Advanced seismic sensors like those used in Atigo Security Systems can detect:
Modern seismic sensors offer several critical advantages over traditional shock sensors:
Atigo’s vibration sensors are specifically engineered for the Indian environment, designed to function reliably in temperatures exceeding 40°C and humidity levels above 90%—conditions where many imported sensors fail.
Atigo’s human detection systems use AI-powered analytics to reduce false alarms by:
While vibration sensors detect the physical attack, advanced motion and presence detection sensors identify unauthorized human activity in and around vault areas:
The intelligence layer is what transforms raw sensor data into actionable security insights. Atigo’s AIoT platform continuously:
For example, if vibration sensors detect drilling activity beneath a vault floor at 2:00 AM while motion sensors indicate no authorized personnel in the area, the AI immediately classifies this as a high-priority intrusion attempt and triggers appropriate responses.
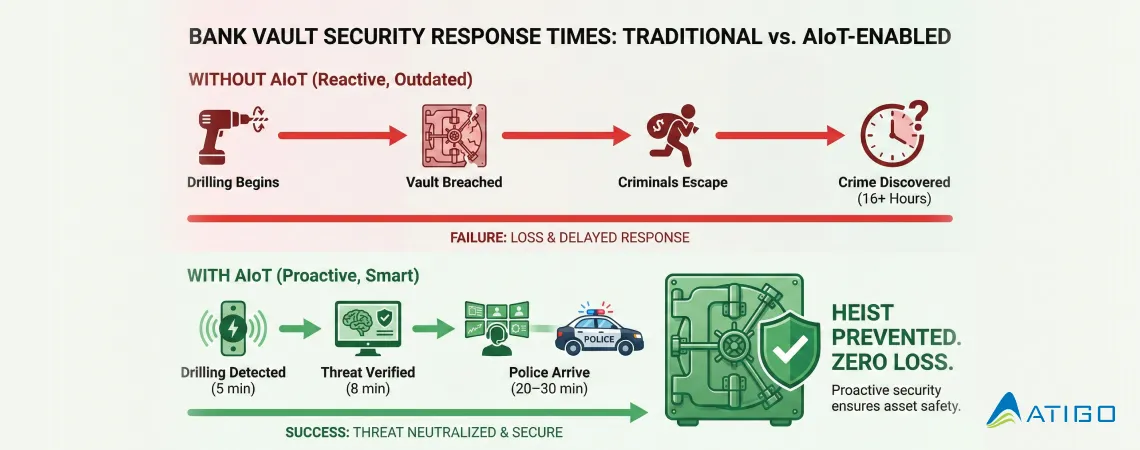
Definition: 24/7 monitoring means trained security analysts staff a central monitoring station around the clock, receiving real-time alerts from connected security systems, verifying genuine threats, and coordinating immediate response with law enforcement and security personnel.
The most sophisticated sensor technology is only as effective as the response it generates. This is where Atigo’s 24/7 Emergency Monitoring Service becomes the crucial differentiator.
Modeled on emergency response systems like the U.S. 911 process and operational since 2013, Atigo’s monitoring center provides:
When sensors detect a potential threat:
For verified threats, monitoring center operators:
Throughout an incident:
In vault break-in scenarios, time is everything. Consider the timeline comparison:
This dramatic compression of detection and response time is the difference between a successful heist resulting in crores of losses and a prevented attempt with zero customer impact.

Atigo isn’t an imported solution adapted for India—it’s a genuinely Made in India technology designed from the ground up for Indian banking conditions:
Atigo’s R&D journey began in 2009 with a specific mission: develop alarm systems that could perform reliably in India’s challenging environment. While imported sensors frequently failed in temperatures exceeding 40°C and humidity above 90%, Atigo engineers created systems specifically engineered to thrive in these conditions.
Following an MoU with the Government of Gujarat at the 2013 Vibrant Gujarat Summit, Atigo committed ₹250 crore to establish advanced R&D and manufacturing facilities in India. Their state-of-the-art facility in Ahmedabad produces everything from copper boards to finished security systems—ensuring quality control, rapid deployment, and ongoing support.
Atigo’s strategic collaboration with IIT Gandhinagar for applied research in AIoT-based safety systems ensures their solutions remain at the cutting edge of security technology. This partnership has enabled development of:
Atigo’s security ecosystem for bank vaults includes:
Launched in 2018, NFire positioned India among the few nations with homegrown wireless addressable fire alarm technology. For bank vaults, this provides:
Released in 2022, Alaris 2.0 is India’s first AIoT security panel offering:
With over 10,000 active installations nationwide and a track record of 500+ emergencies prevented, Atigo has demonstrated real-world effectiveness in protecting India’s most valuable assets.
Atigo’s products meet stringent international and domestic standards as documented on ISO.org and various certification bodies:
This comprehensive certification portfolio ensures that banks implementing Atigo systems meet all regulatory requirements while gaining access to best-in-class security technology.
Before implementing any security upgrades, conduct a thorough vulnerability assessment:
Effective vault protection requires multiple overlapping security layers:
Modern vault security requires intelligent integration, not just sensor addition:
Sensor technology is only half the solution—professional monitoring provides the human intelligence layer:
Technology is most effective when supported by a security-conscious organizational culture:
Consider the full financial impact of a successful vault attack:
For a medium-sized bank branch, a vault breach like those in Kanpur or Navi Mumbai could easily result in total losses exceeding ₹5-10 crore when all factors are considered.
| Cost Component | Traditional Security | AIoT Security (Atigo) |
|---|---|---|
| Initial Installation | ₹1–3 lakh | ₹1–5 lakh |
| Annual Monitoring | ₹50,000–1 lakh (basic) | ₹10,000–20,000 (comprehensive 24/7) |
| False Alarm Costs | High (90–98% false rate) | Low (15–25% false rate) |
| Response Time | ~1 hour | ~60 seconds |
| Prevention Rate | <10% underground attacks | >95% underground attacks |
| Insurance Premium Impact | No reduction | 20–30% reduction |
| 5-Year Total Cost | ₹2.5–5 lakh | ₹50,000–1 lakh |
| Cost of ONE Prevented Breach | N/A (system ineffective) | ₹5–10 crore+ saved |
| ROI Timeline | Negative | < 1 year (after first prevented breach) |
Scenario: Medium bank branch implements Atigo AIoT security
As we look beyond 2026, several trends will shape vault security:
Advanced AI systems will move beyond detection to prediction
Rapid aerial response for reconnaissance:
Vault access will increasingly rely on:
Atigo’s commitment to continuous innovation ensures that banks implementing their systems today are positioned to adopt these future capabilities seamlessly.
As we look beyond 2026, several trends will shape vault security:
Advanced AI systems will move beyond detection to prediction
Rapid aerial response for reconnaissance:
Vault access will increasingly rely on:
Atigo’s commitment to continuous innovation ensures that banks implementing their systems today are positioned to adopt these future capabilities seamlessly.
Underground tunneling and drilling attacks by organized criminal syndicates represent the most significant emerging threat to bank vaults in 2026. Unlike traditional break-ins through doors or windows, these attacks completely bypass conventional security measures by creating unauthorized entry points through basement floors, adjacent properties, or underground tunnels. Recent examples like the December 2025 Gelsenkirchen heist in Germany and similar incidents in Kanpur and Navi Mumbai demonstrate that criminals have mastered this methodology.
Traditional security systems are designed with a fundamental assumption that threats will arrive through conventional entry points—doors, windows, and ground-level walls. They lack sensors to detect vibrations from drilling or tunneling below the vault floor. CCTV cameras can’t see underground activity, perimeter fences don’t extend below ground, and door contact sensors become irrelevant when criminals create their own entry point through basement walls. By the time a traditional system detects a breach, criminals have already accessed the vault.
Based on documented cases, the planning and execution timeline typically ranges from 2-6 months. Criminals often rent adjacent properties weeks or months in advance, conduct extensive reconnaissance, and may spend 20-40 hours actively drilling or excavating tunnels. The actual vault breach and looting often occurs over a weekend or holiday period lasting 24-72 hours when the bank is closed and detection is least likely.
Yes, underground vault attacks are an escalating threat in India. While comprehensive statistics are not publicly available due to underreporting concerns, documented cases in Kanpur (2022), Navi Mumbai (2017), and other locations indicate organized criminal networks are adopting this methodology. The sophistication level of these attacks—involving engineering knowledge, specialized equipment, and extended planning—suggests coordination among professional criminal groups.
Direct losses from documented Indian vault breaches range from ₹1-3 crore in stolen valuables. However, total losses including indirect costs (insurance premium increases, legal fees, reputation damage, regulatory fines, and customer attrition) can easily reach ₹5-10 crore for a medium-sized branch. In extreme cases like the Germany heist, losses exceeded ₹800 crore ($105.7 million).
AIoT (Artificial Intelligence of Things) security adds an AI layer on top of traditional IoT sensors. While IoT security simply collects data from sensors and triggers alerts when thresholds are breached, AIoT security uses machine learning algorithms to analyze patterns, learn normal baselines, distinguish between genuine threats and false alarms, and provide contextual intelligence. For example, an IoT system might trigger an alarm for any vibration, while an AIoT system can differentiate between a delivery truck passing by and the distinctive frequency pattern of a drill boring through concrete.
Seismic vibration sensors use piezoelectric technology to detect minute mechanical oscillations in walls, floors, and foundations. When criminals drill through concrete or excavate tunnels, they create distinctive vibration patterns with specific frequencies and amplitudes. Advanced sensors can detect these vibrations from distances of 10-30 meters away. AI algorithms analyze the vibration signatures to distinguish between normal ambient vibrations (traffic, footsteps, HVAC systems) and attack patterns (drilling, cutting, hammering, excavation). Detection occurs within minutes of drilling commencing—long before any structural breach occurs.
Traditional bank security systems have notoriously high false alarm rates, typically 90-98% according to industry data. This means only 2-10 out of every 100 alarms represent genuine threats. AIoT systems like Atigo’s reduce false alarms to 15-25% through AI-powered pattern recognition and sensor fusion analysis—a reduction of 60-85%. This dramatic improvement means security teams can trust alerts and respond appropriately, while reducing wasted police response costs and alert fatigue among staff.
Atigo’s AIoT security systems use multiple layers of cybersecurity protection specifically to prevent tampering: (1) Military-grade AES-256 encryption for all data transmission, (2) Multi-channel redundancy (Wi-Fi, GSM, Bluetooth) so disabling one connection doesn’t compromise the system, (3) Continuous health monitoring that alerts the monitoring center if any sensor is tampered with or disconnected, (4) Physical security measures on sensor housings to prevent unauthorized access. While no security system is 100% tamper-proof, AIoT systems are significantly more resistant to manipulation than traditional systems due to their distributed, encrypted, and continuously monitored architecture.
24/7 monitoring means trained security analysts staff a central monitoring station around the clock. When AIoT sensors detect a potential threat, alerts are transmitted instantly to the monitoring center where analysts review sensor data and video feeds, verify genuine threats using AI-assisted decision support, and coordinate immediate response with police and bank security. Human verification is critical because it: (1) Filters out remaining false alarms before police are dispatched, (2) Provides context and real-time intelligence to responding officers, (3) Ensures immediate escalation of verified threats, and (4) Maintains continuous situational awareness throughout an incident. Automated systems alone cannot provide this level of intelligent response.
A complete AIoT security system for a typical bank branch vault requires an initial investment of ₹15-25 lakh for hardware installation (sensors, control panels, networking equipment) plus ₹3-5 lakh in annual monitoring service fees. Costs vary based on vault size, number of sensors required, existing infrastructure compatibility, and specific features implemented. However, considering that a single prevented vault breach can save ₹5-10 crore in total losses, the ROI is typically achieved within 1-2 years.
Full implementation from initial assessment to complete activation typically takes 3-4 months: Month 1 for comprehensive security audit and architecture design, Month 2 for procurement and site preparation, Month 3 for sensor installation and system integration, and Month 4 for staff training, testing, and go-live. However, critical protection can be deployed faster in high-risk situations—basic seismic sensor coverage with monitoring can be operational within 2-3 weeks if needed urgently.
Yes, Atigo’s AIoT systems are designed for seamless integration with existing infrastructure. The Alaris 2.0 control panel can interface with existing CCTV systems, access control platforms, building management systems, and legacy alarm sensors. This means banks don’t need to completely replace their current security investments—AIoT sensors augment and enhance existing capabilities by filling the underground detection gap and adding AI-powered intelligence layer to all security data.
Atigo’s systems are designed to work with existing network infrastructure in most cases. The Alaris 2.0 panel supports multiple connectivity options (Wi-Fi, GSM cellular, Bluetooth) ensuring redundant communication even if primary internet fails. Bandwidth requirements are minimal (typically <100 KB/s for sensor data) as the AI processing occurs locally on the control panel with only alerts and status updates transmitted to the monitoring center. However, for optimal performance, banks should ensure reliable internet connectivity with backup cellular failover.
Atigo systems include multiple backup mechanisms: (1) Battery backup provides 8-24 hours of continuous operation during power outages, (2) Multi-channel connectivity means if Wi-Fi internet fails, the system automatically switches to GSM cellular connection, (3) The monitoring center receives immediate alerts if any system component loses power or connectivity, and (4) All sensor data is stored locally on the control panel so no information is lost during temporary outages. These redundancies ensure criminals cannot disable the system by simply cutting power or internet cables.
A complete AIoT security system for a typical bank branch vault requires an initial investment of ₹15-25 lakh for hardware installation (sensors, control panels, networking equipment) plus ₹3-5 lakh in annual monitoring service fees. Costs vary based on vault size, number of sensors required, existing infrastructure compatibility, and specific features implemented. However, considering that a single prevented vault breach can save ₹5-10 crore in total losses, the ROI is typically achieved within 1-2 years.
Atigo offers several unique advantages specifically for Indian banks: (1) Indigenous engineering for Indian conditions (40°C+ temperatures, 90%+ humidity) where imported sensors often fail, (2) Local manufacturing and support ensures rapid deployment, spare parts availability, and responsive service, (3) Understanding of Indian banking operations, RBI compliance requirements, and local threat landscape, (4) Cost-effective pricing compared to imported solutions (typically 30-40% lower total cost of ownership), (5) Proven track record with 10,000+ installations including State Bank of India, Indian Railways, and other critical infrastructure, (6) IIT Gandhinagar research partnership ensures cutting-edge technology development, and (7) “Made in India” supports Atmanirbhar Bharat initiative while ensuring technology sovereignty.
Atigo products meet comprehensive international and domestic certification standards: ISO 9001 (Quality Management), CE Marking (European Conformity), RoHS (Environmental Compliance), STQC (Government of India quality testing), EN54 (European fire detection standard), and IS/ISO 7240 (Indian fire safety standards). These certifications ensure that banks implementing Atigo systems meet all RBI regulatory requirements and can confidently deploy the technology in compliance with banking security standards.
Yes, Atigo has deployed security systems across numerous banking and financial institutions including State Bank of India (SBI) and multiple public and private sector banks. Due to security and confidentiality considerations, specific branch locations and detailed case studies are shared during private discussions with prospective clients. Atigo can facilitate reference calls with existing banking clients and arrange site visits to observe operational systems upon request during the evaluation process.
Atigo provides comprehensive training and support including: (1) On-site training for security personnel, branch managers, and IT staff during installation, (2) Detailed operation manuals and quick-reference guides, (3) Quarterly refresher training sessions, (4) 24/7 technical support hotline for troubleshooting, (5) Remote diagnostics and system health monitoring, (6) Annual on-site system audits and optimization, (7) Software updates and security patches deployed remotely, and (8) Emergency response coordination training with local police. Support is delivered in regional languages as needed to ensure all staff can effectively operate the system.
Atigo’s monitoring center has processed alerts from over 10,000 active installations nationwide and successfully prevented over 500 genuine emergencies across fire, intrusion, and security threats since operations began in 2013. Critically, monitored sites with Atigo’s comprehensive AIoT security have maintained a 100% record of zero successful vault breaches—meaning no bank vault protected by Atigo’s full AIoT sensor suite with 24/7 monitoring has suffered a completed underground attack. This real-world prevention record demonstrates the effectiveness of early detection and rapid response in stopping organized criminal operations before they succeed.
The December 2025 Gelsenkirchen heist, combined with India’s own history of tunnel-based vault attacks in Kanpur and Navi Mumbai, delivers an unmistakable message: traditional vault security is obsolete. Organized criminals have demonstrated they can circumvent conventional defenses with planning, patience, and precision.
Indian banks face a choice in 2026:
The technology exists. The proven solution is available. Atigo Security Systems has demonstrated—through over a decade of operations, 10,000+ installations, and 500+ prevented emergencies—that AIoT-based early detection security works in Indian conditions.
The question is not whether underground vault attacks will continue to occur—the Gelsenkirchen heist proves criminals have mastered this methodology. The question is: Will your bank’s vault be prepared when organized criminals come calling?
In 2026, the best vault security is not the thickest walls or the heaviest doors. It’s the intelligent sensors that detect threats before walls are breached, combined with 24/7 monitoring that ensures human intelligence backs technological capability.
Don’t wait for an incident to drive change. Contact Atigo Security Systems today for a complimentary vault security assessment. Their team of experts will:
Atigo Security Systems
Website: www.atigo.in
Email: info@atigo.in
Phone: Available on website
Made in India. Trusted Nationwide. Protecting What Matters Most.
With 12 years of innovation excellence, partnerships with IIT Gandhinagar, ₹250 crore investment in indigenous R&D and manufacturing, and trust from India’s leading institutions including Indian Railways, India Post, SBI, Tata Group companies, and Adani Power, Atigo brings world-class security technology engineered specifically for Indian conditions.
The vault you save may be your own. Contact Atigo Security Systems today.
Author Expertise: This article draws on extensive research of recent international and domestic vault security incidents, Reserve Bank of India cybersecurity guidelines, AIoT security technology developments, and Atigo Security Systems’ documented track record in protecting India’s critical infrastructure.
Sources Cited:
India’s trusted security partner since 2013. Made in India manufacturer of 24/7 monitored alarm systems.
© 2013-2025 Atigo Security — A division of Atigo Enterprises Limited
Made in India. Monitored in India.